Security Service
Definition
Sakai provides a two-tier security system designed to authorize users to perform a specified function against an entity or collection of entities. Security is implemented using AuthZGroups that provide a way to group users (membership), define a role for each of them, and define permissions associated with a particular role in that group context.
See also Permission Helpers.
Common Data Elements
The following data elements are included the AuthZGroup object:
Element | Description |
|---|---|
Entity | All entity data elements are included. |
Members | User members in this group. |
Roles | Roles defined for this group. |
Provided Id | An external id used with the group provider. |
The following data elements are included in the Role object:
Element | Description |
|---|---|
Id | An identifier for this role. |
Description | A textual description of this role. |
Functions | The functions associated with the role. |
The following data elements are included in the Member object:
Element | Description |
|---|---|
User id | The user member. |
Role | The user's role in this group. |
Active Flag | Indicates how active the user is. |
Metadata
All Sakai entities may have an arbitrary number of properties associated with them. While all of these properties are optional, certain properties are commonly used such as who created or modified, creation or modified time-date, etc.
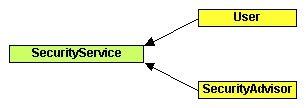
The Security Service
The Security Service is defined using a lock and key descriptive paradigm. Creating a key defines a authorization grant. Unlocking a resource tests for authorized access to perform a function on that resource (or collection). The Security Service also allows SecurityAdvisors to be created and added (in a stack order). Advisors enable policies to be defined that potentially override default group permissions.
The AuthzGroup Service
The AuthzGroupService provides methods for managing AuthzGroups. It allows groups to be created, added, removed, and found. Methods are provided to manage membership and test for authorization to perform functions in a particular group given the role of the active user.
The Function Manager
Allows functions to be registered with Sakai. A list of all functions can be gotten, or a list given a prefix. Current convention is to use an application prefix separated by a dot, such as "app.update". This allows the functions associated with an application or tool to be gotten.
The Group Provider
The following methods are included in the GroupProvider API:
- String getRole(String id, String user);
- Map getUserRolesForGroup(String id);
- Map getGroupRolesForUser(String userId);
- String[] unpackId(String id);
Note that this interface is largely used to determine the role of a user in an externally defined group. It doesn't provide a large enough interface to move autorization outside of Sakai.
Note also that group ids for provided sites may be different than the internal Sakai representation. If corresponding realms are being maintained in Sakai (this is the typical case), then a provisional Id is also kept and is passed as the group Id when provider calls are made. Furthermore, this provided group Id may be a compound id with several external group ids concatenated using "+" as a delimiter.
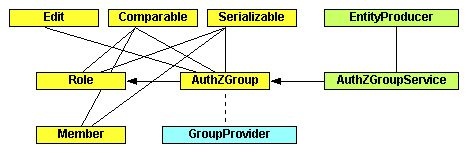
Objects
The following objects are included in the Sakai authz interface:
AuthzGroup.java
AuthzGroupService.java
GroupProvider.java
Member.java
Role.java
The following objects have been added to this module for 2.2:
SecurityAdvisor.java
SecurityService.java
PermissionsHelper.java
FunctionManager.java
Exceptions moved or added for 2.2:
AuthzPermissionException.java
GroupAlreadyDefinedException.java
GroupIdInvalidException.java
GroupNotDefinedException.java
RoleAlreadyDefinedException.java
See also: